Stateless Authentication Persistence: Unpacking the Power of JWTs
Navigating the Tokenized Future of Secure User Sessions
In the ever-evolving realm of web development, ensuring user authentication persists seamlessly across sessions is paramount. Stateless session storage, primarily using JWTs (JSON Web Tokens), has become the go-to choice for modern applications. Let's delve deeper into this mechanism and understand its advantages and intricacies.
JWT: The Modern Keystone for Stateless Persistence
JSON Web Tokens represent a breakthrough in how we think about authentication. It's not just a mere token; it's a compact, self-contained way to convey information between parties. This information, being digitally signed, means it's both verifiable and trustworthy. The beauty lies in its self-reliance - a JWT can validate its own authenticity without the server having to store any session-related data. This drastically reduces the overhead and potential bottlenecks in high-traffic scenarios.
Imagine a secure box - the JWT. Within this box, three integral components reside:
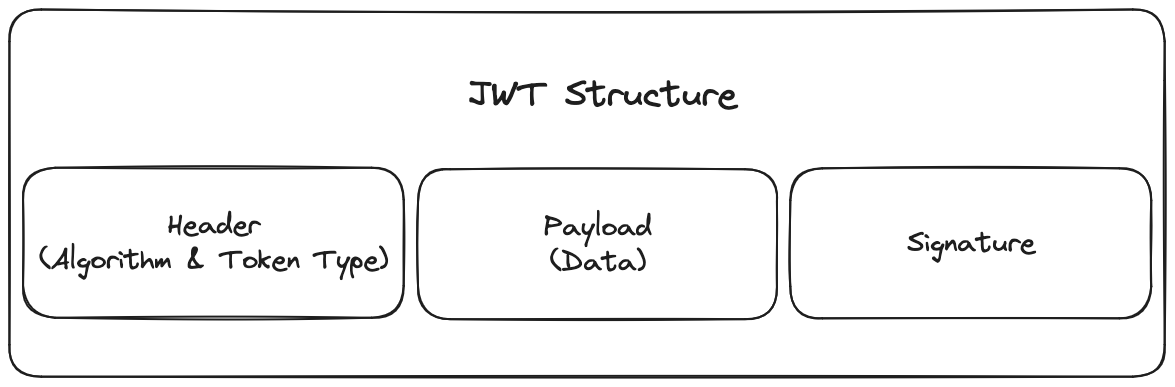
Header: Think of the header as the label of our JWT box. It declares the type of token and the algorithm used for the signature, usually represented in the structured JSON format.
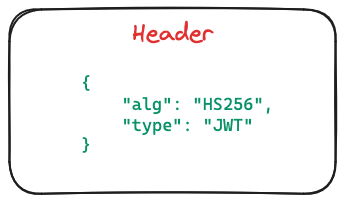
Payload: This is the core of the JWT, housing the actual data we wish to communicate. This data could range from user IDs to user roles and other pertinent details. Like the header, the payload also utilizes the JSON format, ensuring clarity and compatibility.
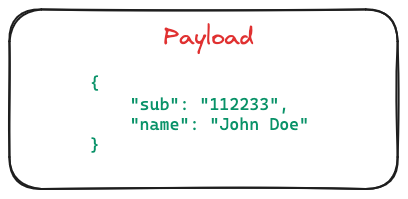
Signature: The signature is the JWT's guardian. Formed using a combination of the header, payload, and a secret, this signature ensures that the JWT remains uncompromised during its journey. It acts as a seal, vouching for the integrity of the enclosed data.
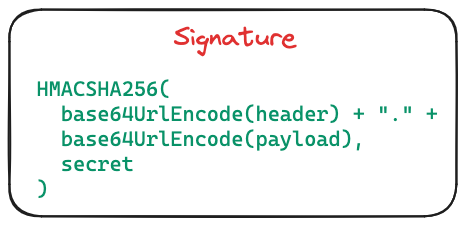
When a JWT is dispatched, the recipient server deciphers the header and payload. The signature guarantees the message's authenticity, ensuring the data remains untampered.
The header and payload above with some secret of our choice encodes into
// Our JSON Web Token
"eyJhbGciOiJIUzI1NiIsInR5cGUiOiJKV1QifQ.eyJzdWIiOiIxMTIyMzMiLCJuYW1lIjoiSm9obiBEb2UifQ.XALg0Y5SdDxrSjlf6qCbdhyKUMauufIAFGN5PS-amGU"
This is our header, payload and signature as 3 parts separated by a dot and base64 encoded. We can see the contents by using any base64 decoder.
const token = "eyJhbGciOiJIUzI1NiIsInR5cGUiOiJKV1QifQ.eyJzdWIiOiIxMTIyMzMiLCJuYW1lIjoiSm9obiBEb2UifQ.XALg0Y5SdDxrSjlf6qCbdhyKUMauufIAFGN5PS-amGU"
token.split(".").forEach((part) => console.log(atob(part)));
/* Output:
{"alg":"HS256","type":"JWT"}
{"sub":"112233","name":"John Doe"}
l�MÛ�Ü��á�EyC���ò_*�ÛM)ñ�L�ä2«�Û
*/
As we can see by the output of decoding, we see our exact header and payload data.
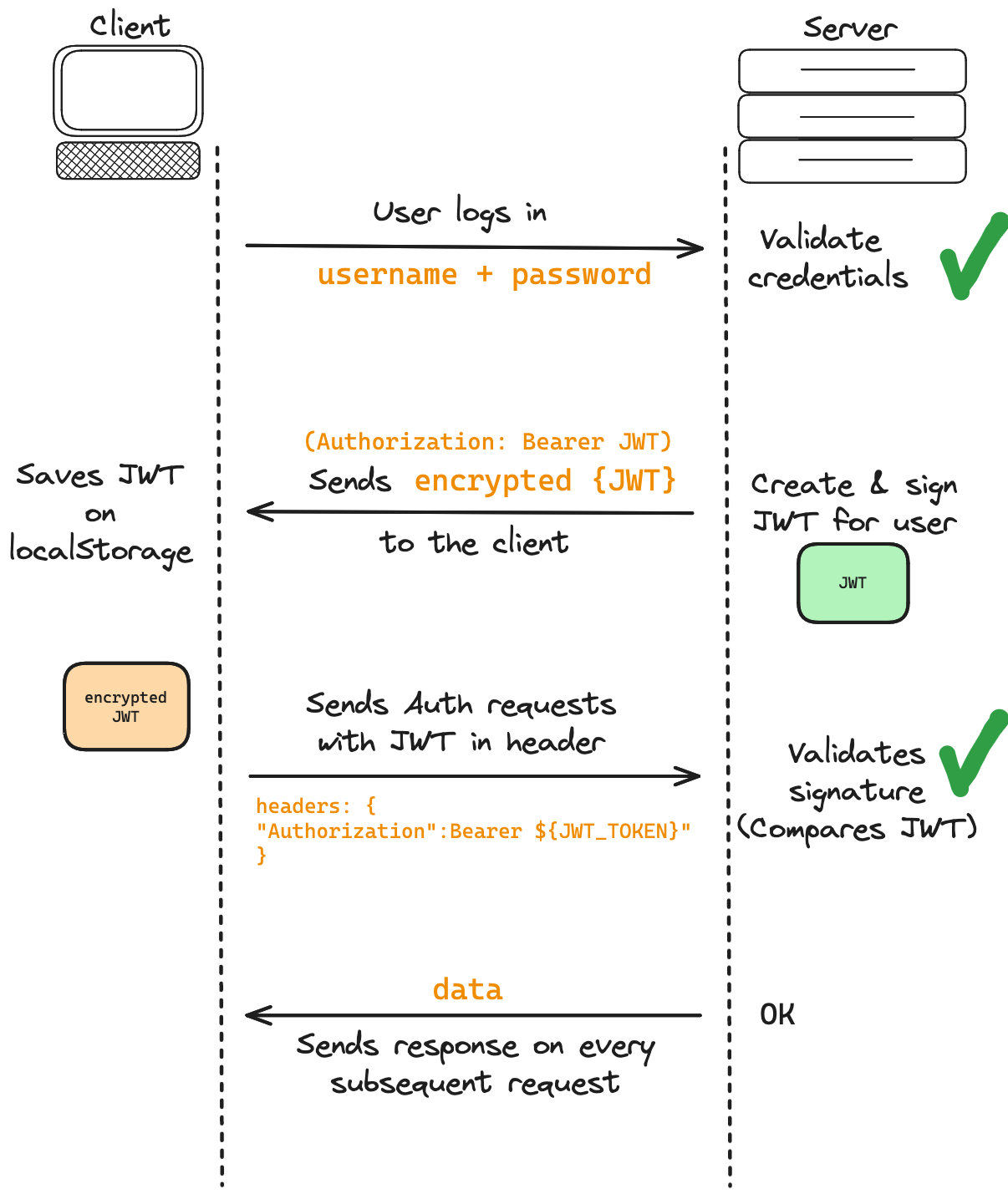
JWT-based Authentication Flow: A Step-by-Step Explanation
-
User Login Request: The process starts when a user attempts to access a secured resource. The user provides their credentials, typically a username and password.
-
Server-side Validation: Upon receiving the credentials, the server validates them against its database or another trusted authority. If the credentials are correct, the server prepares to generate a JWT for the user.
-
Creation of JWT: The server then creates a JWT. This token encapsulates certain user information (like user ID, roles, or other claims) in its payload. This token is then signed using a secret key, ensuring that it can be trusted and hasn't been tampered with.
-
Sending JWT to the Client: Once the JWT is generated and signed, the server sends it back to the client. This JWT serves as proof of authentication and authorization for the user.
-
Storing the JWT on the Client: When the client receives the JWT, it stores the token, often in a place like the local storage. This storage ensures that the client doesn't need to re-authenticate for every request it makes.
-
Authenticated Requests: Now, every time the client wants to access a secured resource or make any request that requires authentication, it attaches the stored JWT in the request header. This token acts as a proof of the user's identity and permissions.
-
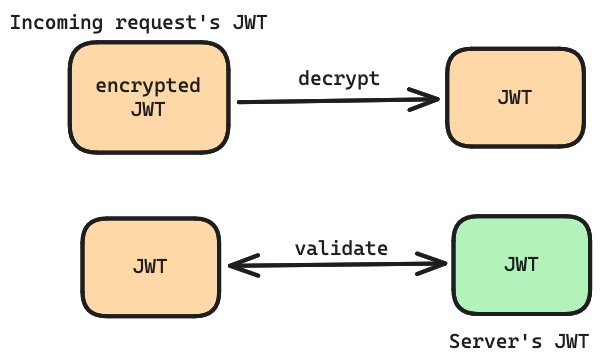
Server-side Verification: On receiving a request with a JWT, the server doesn't need to recheck the user's credentials in its primary database. Instead, it simply verifies the JWT's signature using its secret key. If the signature matches, it means the token is legitimate and hasn't been tampered with.
-
Server Response: After verifying the JWT, the server processes the client's request. Depending on the user information encoded within the JWT and the user's permissions, the server sends back the appropriate response or data.
Pros and Cons of JSON Web Tokens
JSON Web Tokens (JWTs) have become a predominant authentication mechanism in today's digital landscape. It's essential to appreciate their strengths and acknowledge their limitations. Let's dive into the pros and cons:
Pros:
Portability: JWTs encapsulate verifiable claims. Their self-contained nature enables cross-service verification without recurrent validation checks, enhancing portability in distributed systems.
Scalability: Stateless Authentication: By shifting from stateful to stateless authentication, JWTs remove the need for server-side session storage. This facilitates easier scaling of applications in environments with a vast number of users.
Flexibility & Performance: JWTs provide a unified method for authentication across different platforms, such as mobile and web apps. Their format standardizes data sharing, promoting integration between disparate systems.
Robust Security: JWTs benefit from cryptographic security. Their stateless attribute nullifies certain attack vectors like session hijacking.
Cons and Security Concerns:
Compromised Secret Key: At the heart of JWT's cryptographic assurances lies the secret key. If an attacker uncovers this key, it spells disaster. The key's exposure leads directly to the forging of tokens, opening up systems to unauthorized breaches.
Visibility of Payload: While JWTs carry encoded information, this isn't synonymous with encryption. Anyone who obtains the token can decode its contents. Sensitive data within the payload is at risk unless additional encryption is applied.
Expiration Limitations: The inherent temporality of JWTs is a double-edged sword. If tokens are short-lived, they bolster security but may lead to frequent user re-authentications, potentially hindering the user experience. However, long-lived tokens, while user-friendly, become prolonged security liabilities.
Transmission Risks: Without secure channels, JWTs are vulnerable in transit. If not conveyed over protocols like HTTPS, these tokens can fall into malevolent hands, granting attackers unauthorized access.
Algorithm Manipulation: JWTs rely on algorithm specifications for their operations. But misconfigurations or lax validation can result in systems accepting manipulated algorithm headers, making them susceptible to attacks.
Token Exposure: Whether through cross-site scripting (XSS) attacks or other means, JWTs can inadvertently leak. Such leaks pose dire consequences, with attackers gaining the ability to impersonate legitimate users or access restricted data.
Revocation Hurdles: One of JWT's strengths—its statelessness—becomes a challenge when tokens need invalidation. Especially in systems where permissions change dynamically, the inherent inflexibility of JWTs regarding revocation becomes evident. Blacklisting tokens can be a solution, but it reintroduces state and complexity into the system.
In light of these considerations, while JWTs offer compelling advantages, they come with their own set of challenges, especially from a security standpoint. Understanding these intricacies is paramount for developers and architects aiming to construct secure, efficient, and user-centric digital solutions.
Alternatives to JWT
While JWTs are a popular choice in today's digital landscape, various other authentication mechanisms have also proven their worth over time. Here's a very brief overview:
Session Tokens: Traditional methods using random strings linked to a user's session. They're stored in cookies or server-side and are direct but not entirely stateless.
Single Sign-On (SSO): Allows users to log in once for multiple applications. It centralizes authentication but can have a single point of failure.
OAuth 2.0: Primarily an authorization framework, OAuth 2.0 allows third-party apps to access user accounts without revealing credentials, using granted tokens.
OpenID Connect (OIDC): An extension of OAuth 2.0, OIDC introduces an identity layer for verifying end-user identity. While OIDC tokens often utilize JWT format, they serve a distinct role in authenticating the end-user.
Understanding these options helps developers choose the right authentication method, harmonizing user experience, security, and scalability.
In conclusion, with JWTs at the core of stateless authentication persistence, modern web applications benefit from enhanced scalability, portability, and efficiency. While JWTs offer numerous advantages, it's equally important to understand their limitations. Such awareness empowers developers and architects to craft secure, responsive, and user-centric applications.